Configure Conditional Access Rules and MFA
The User Management Pack 365 SP Edition Tenant account should be excluded from the Conditional Access rules that forces session reauthentications. Conditional Access allows administrators to enforce access controls based on specific conditions within an existing policy. For example, to allow access from User Management Pack 365 SP Edition server in a Trusted location.
This step is mandatory. Failure to implement these rules will lead to token invalidation expiration, and as a result, you will not be able to connect to the customers' M365 platform for onboarding and M365 synchronization operations. For more information, see Conditional Access Rules.
A Delegated Access Token may become invalid due to the following:
|
■
|
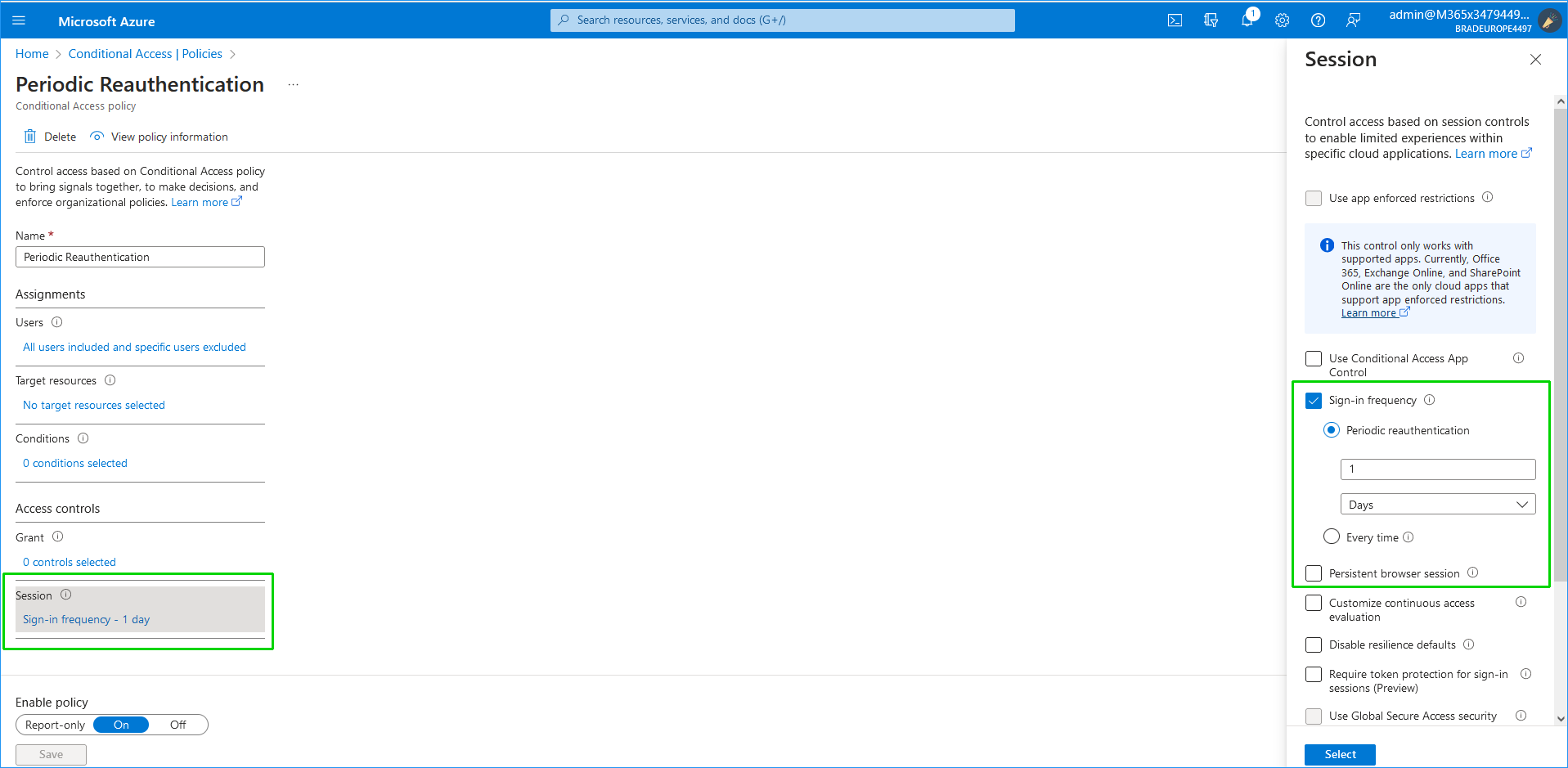
Sign-in frequency time period before a user is prompted to sign in again when attempting to access the Token connection. The frequency of reauthentication may be specified in hours or days, or it can be set every time you use the Token connection. |
|
■
|
Persistent Browser Session controls the persistence of the authentication session token in the browser. If the session token expires or becomes invalid, the user needs to reauthenticate, potentially invalidating the Delegated Access Token. |
When implementing Multi-Factor Authentication (MFA) in Azure, the re-authentication process utilizes the Sign-in frequency time. In the absence of enabled conditional access policies, the Microsoft Entra ID default configuration for user sign-in frequency is a rolling window of 90 days (users are not prompted to reauthenticate within this window). Consequently, we also recommended to configure the per-User MFA Settings to 365 days (see procedure below) to prevent recurring downtime due to token invalidity during this period.
|
1.
|
Login to the Azure portal with Global Admin permissions (https://portal.azure.com/#home). |
|
2.
|
In the Manage Microsoft Entra ID, click View. |
|
3.
|
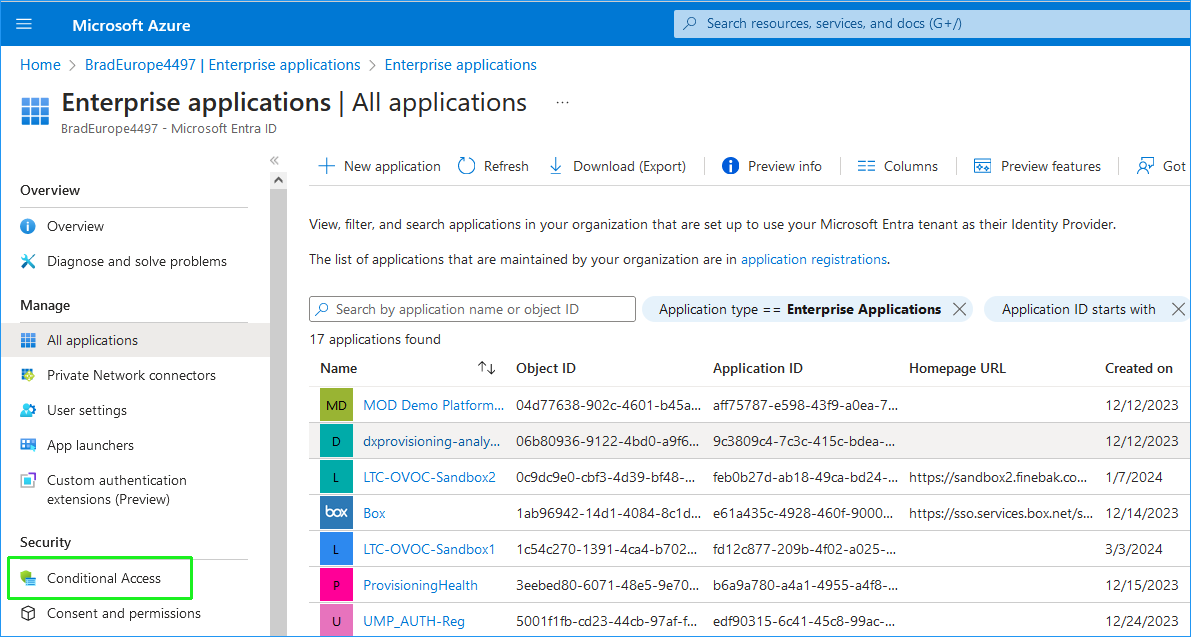
In the Navigation pane select Enterprise applications. Alternatively you may navigate to the same screen by searching for “Enterprise applications” in the global search bar. |
|
4.
|
In the Navigation pane, select Conditional Access. |
|
5.
|
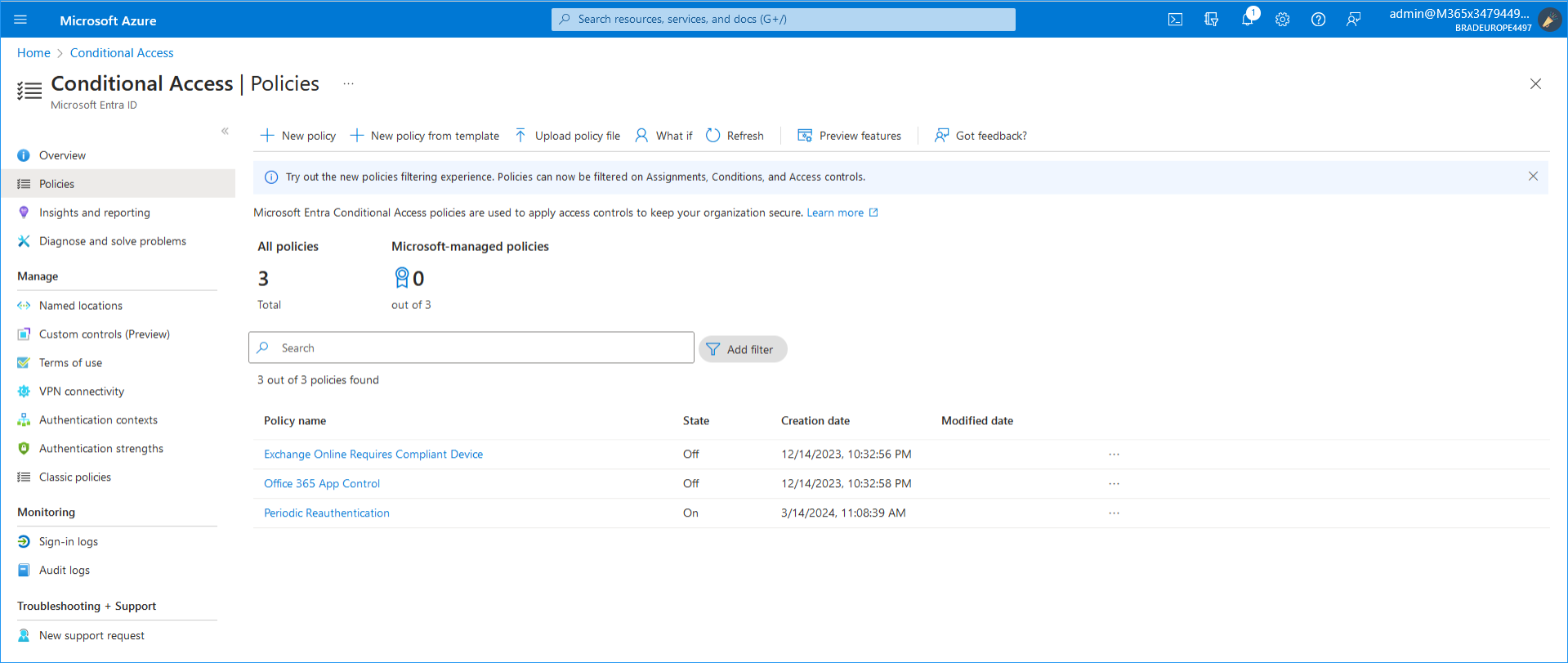
In the Navigation pane, click Policies. |
|
6.
|
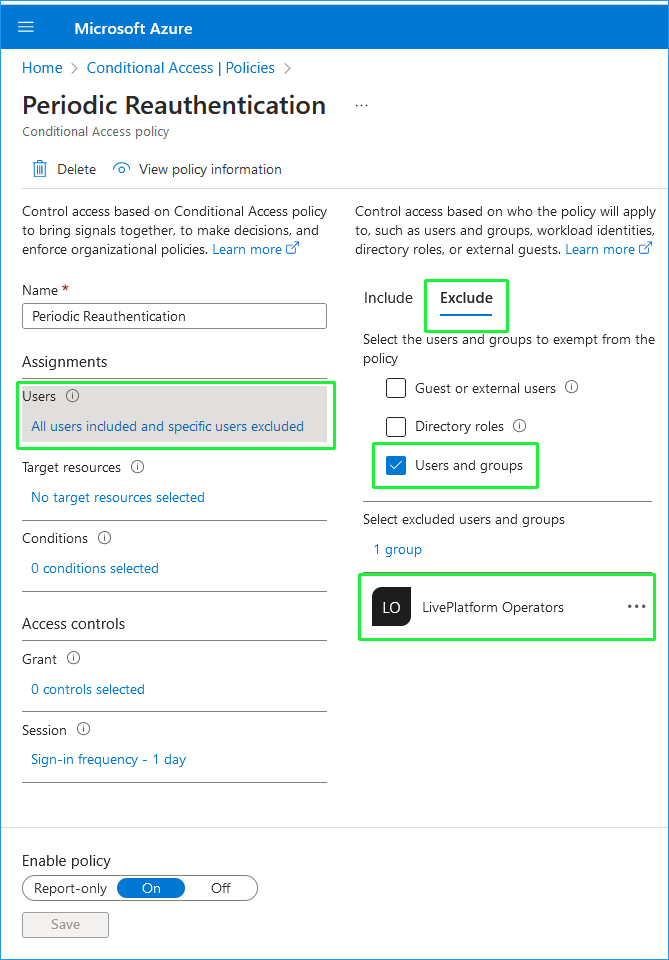
Select a policy, for example Periodic reauthentication. |
|
7.
|
Check whether one of the following options is configured under Access controls > Session: |
|
●
|
Persistent browser session |
|
8.
|
If yes, then in the Users section configure the User Management Pack 365 SP Edition service account to be excluded from the policy. |
|
9.
|
Repeat the above steps for each configured policy that would contain the policies mentioned in step 7. |
The above steps are related to the Conditional Access Policies. The below steps configure the Azure Global "remember multi-factor authentication" adjustment to 365 days.
|
10.
|
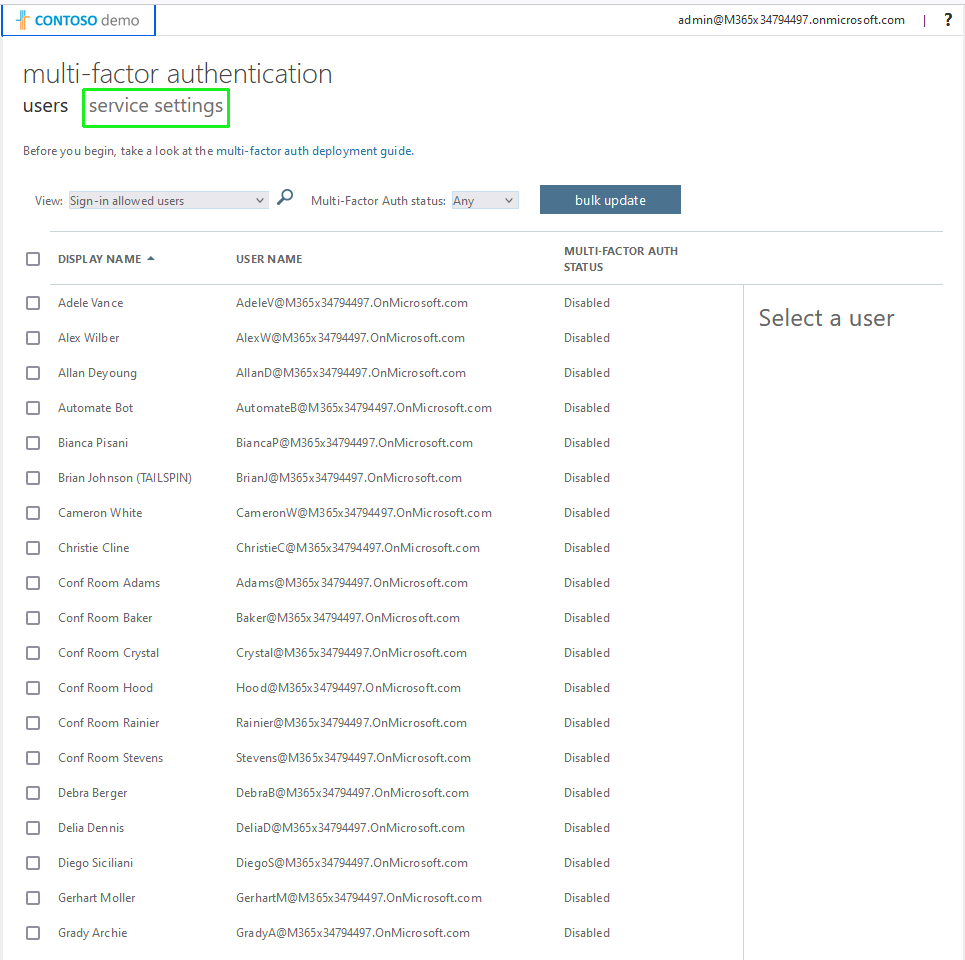
In the Users screen, click Per-user MFA. |

|
11.
|
Click Service Settings. |
|
12.
|
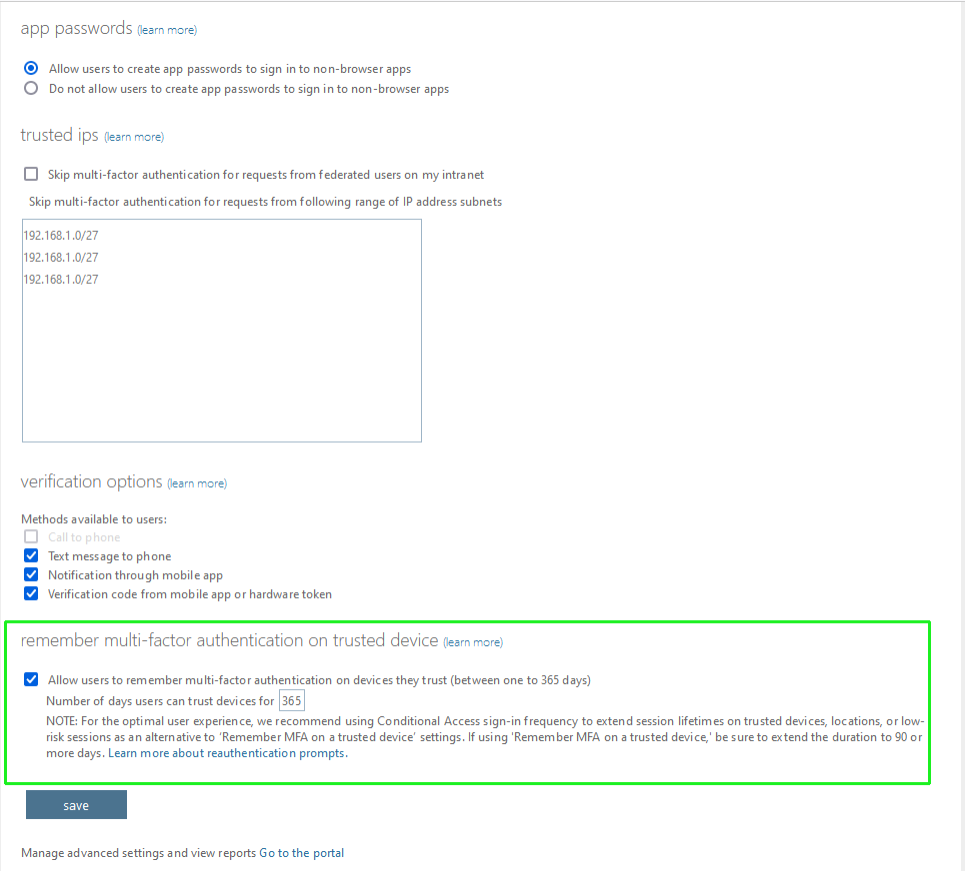
Check the box 'Allow users to remember multi-factor authentication on devices they trust'. Set the parameter 'Number of days users can trust devices for' to 365. |







